Password managers
Set up XPipe to retrieve passwords from an external password manager
Introduction
Via the available password manager integrations, you can configure XPipe to retrieve passwords from your locally installed password manager. That way, XPipe doesn't have to store any secrets itself, they are only queried at runtime.
Learn how to configure your password manager to work with XPipe.
Using credentials for connections
Learn how use credentials from a password manager within XPipe.
Using SSH keys from your password manager
If your password manager supports SSH keys, learn how to use them in XPipe.
Integrations
There are various different integrations available for many popular password managers. You can find the setup instructions for each listed one here.
You can enable a password manager integration in the settings menu:
1Password
The 1Password integration requires you to first install the 1Password CLI and add it to the PATH. This executable is not included in the normal 1Password installation, so you will have to install it manually:
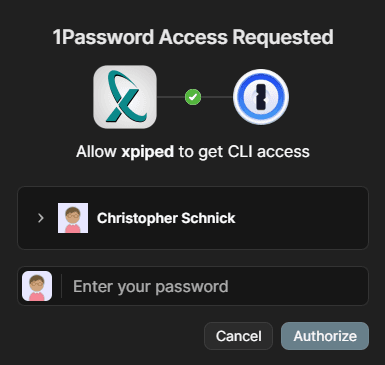
Once the op command is set up, you can instantly use 1Password from XPipe. You will have to confirm the first access request to the vault, but afterwards it will work automatically without user input:
Key format
The 1Password integration supports two different formats of password references. You can choose to just specify the item name in XPipe. This will look up the item in the default 1Password vault. If you are using multiple vaults, however, this might result in entries not being found if they are not in the default vault.
For these cases, there is also the 1Password op:// URL scheme, which allows you to also specify the specific vault to use. For more information, see the 1Password docs. In short, these references have the form of op://<vault>/<item>/password, so for example op://personal/myitem/password to retrieve the item myitem in the personal vault.
KeePassXC
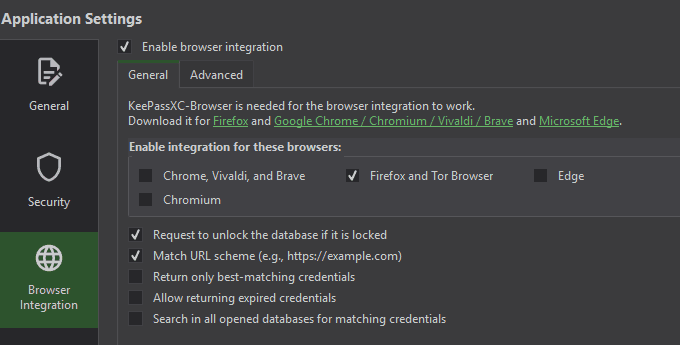
The KeePassXC integration works over the KeePassXC browser extension interface, meaning that it will handle the same way as the KeePassXC browser extensions if you have them installed. For the integration to work, you first have to enable the browser integration in KeePassXC at Tools -> Settings (The browser type checkboxes don't matter here):
Then, upon the first request from XPipe, you should be prompted to allow XPipe to access your database, assuming that it is unlocked:
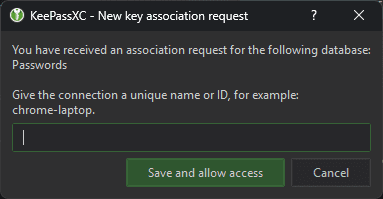
If you confirm this, XPipe will be able to retrieve passwords from KeePassXC.
Item URLs
Note that since XPipe uses the browser integration, XPipe can only access entries by their URL, not their name. Any entry has to be referenced by the URL field. In practice, the URL field doesn't have to be a valid URL; any name will also suffice.
The KeePassXC logic for finding a matching URL might sometimes get confused, e.g. when you use something like subdomains. KeePassXC does not perform exact matching and instead parses the URL and finds the closest one. It is recommended to name entries like sub1_example_com and sub2_example_com instead of sub1.example.com and sub2.example.com. The latter might result in unintended behavior and return multiple entries for any example.com entry you query from XPipe.
Multiple databases
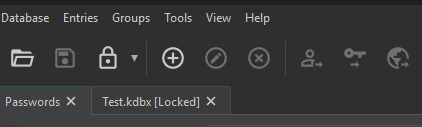
You can also use multiple separate databases at the same time in KeePassXC:
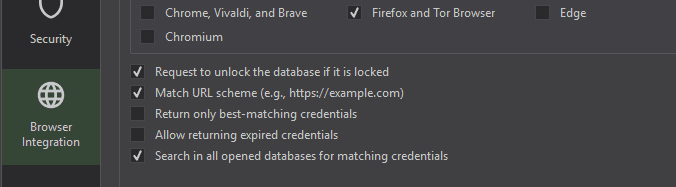
XPipe supports accessing multiple databases, assuming that each one is linked and the Search in all databases option is enabled in KeePassXC:
Bitwarden
The Bitwarden integration requires you to first install the Bitwarden CLI and add it to the PATH. This executable is not included in the normal Bitwarden installation, so you will have to install it manually.
Once the bw command is set up, you will first have to log in initially via bw login. For more information on logging into the Bitwarden CLI, see the Bitwarden docs.
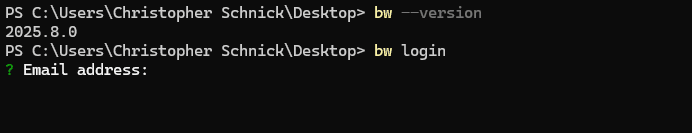
After that is done, you can start interacting with Bitwarden from XPipe. On the first use of the Bitwarden integration during an XPipe session, you will have to enter your vault passphrase to unlock the vault:
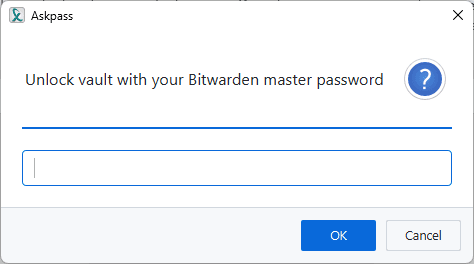
Then, XPipe will be able to retrieve passwords from Bitwarden during the session using the item name of the password entry. For example, you could retrieve the credentials for the following item by specifying the item name example-item in XPipe:
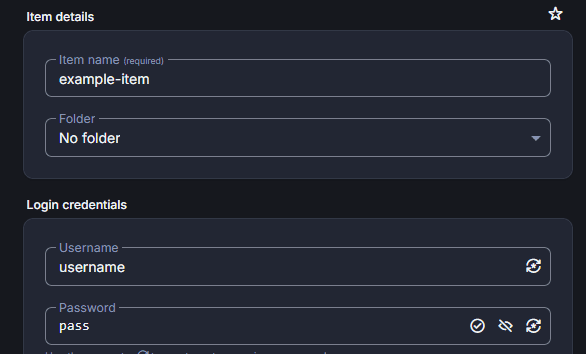
Note that it is not recommended to use the snap or flatpak version of the bw CLI. If you encounter issues with it not working at all or XPipe is continuously asking for the master password, try to use another bw CLI package distribution.
Dashlane
The Dashlane integration requires you to first install the Dashlane CLI and add it to the PATH. This executable is not included in the normal Dashlane installation, so you will have to install it manually:
Once the dcli command is set up, you will first have to log in initially when XPipe first connects to the Dashlane vault. Afterward, XPipe will be able to retrieve passwords from Dashlane during the session using the entry's item name.
Keeper
The Keeper integration requires you to first install the Keeper Commander CLI and add it to the PATH. This executable is not included in the normal Keeper installation, so you will have to install it manually:
Once the keeper-commander command is set up, you will first have to log in to your Keeper account initially when XPipe connects to the vault:
If you are logged in, XPipe will be able to unlock the vault. For that, XPipe will initially prompt for the master password when Keeper is first used during a session:
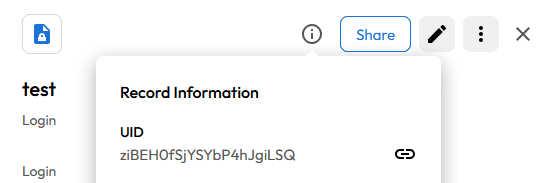
Then, XPipe will be able to retrieve passwords from Keeper during the session using the record's UID, which you can look up for an entry in the Keeper vault interface:
2-Factor authentication
If your Keeper account requires a 2FA login via an Authenticator app, you will have to configure XPipe to expect this via the dedicated option:

This will additionally ask for a 2FA code from your authenticator device when a new password is queried. By default, you will need to provide a new 2FA code for each Keeper item that is requested during an XPipe session.
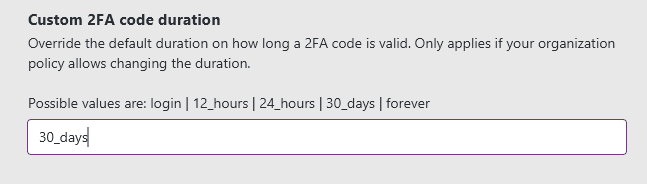
If you want the Keeper CLI to not ask every time for a 2FA code and your administrative Keeper configuration allows it, you can change this requirement to ask less often by specifying a custom duration setting:
Passbolt
The Passbolt integration requires you to first install the Passbolt CLI and add it to the PATH:
Once the passbolt command is set up, you will have to enter the configuration data of your passbolt server in XPipe. You need the server URL, the gpg private key, and the passphrase from the profile settings page:
Once you have entered them in the XPipe settings menu, you need to obtain the resource UUID for every password resource you want to use. You can find this ID in the permalink URL for an entry, which you can find at the Copy permalink option:
The integration also supports using your existing CLI config if that is configured. If you are using MFA with TOTP, this is actually required as the MFA prompt can not be filled in a non-interactive mode. See https://github.com/passbolt/go-passbolt-cli?tab=readme-ov-file#mfa on how to configure the passbolt CLI for noninteractive TOTP.
Psono
The Psono integration requires you to first install the Psono CLI and add it to the PATH:
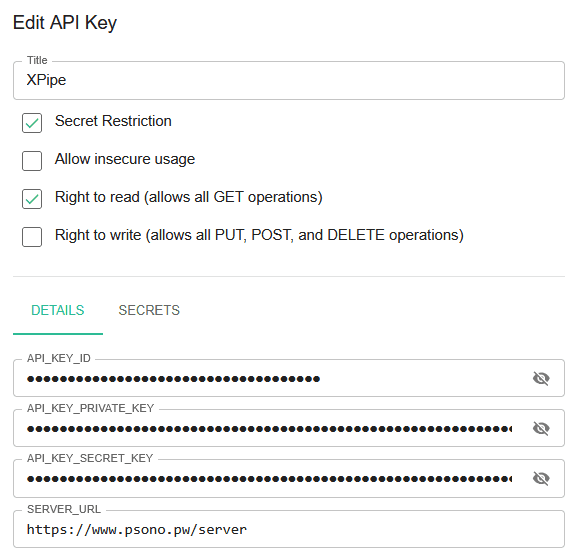
Once the psonoci command is set up, you will have to enter the data of an API key. You can read about how to create one here. You need the API key ID, API key secret key, and server URL from the API key page:
Once you have entered them in the XPipe settings menu, you need to obtain the secret ID for every associated secret. You can associate secrets with this API key in the secrets tab on the same page:
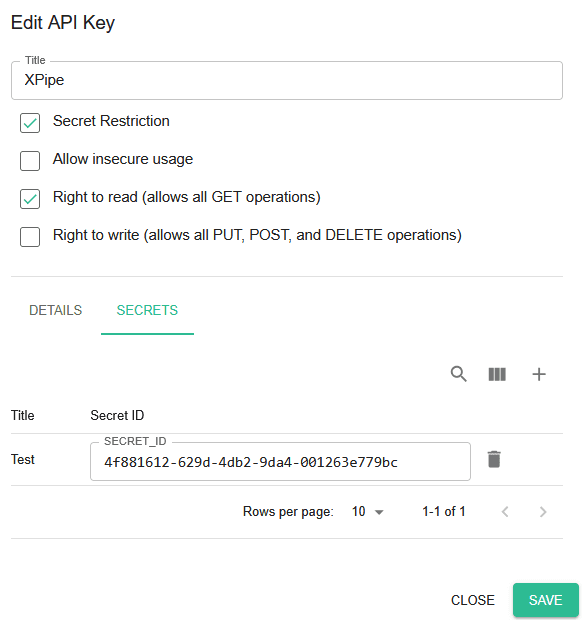
Only secrets that are added to the API key can be queried. The secret ID is specific to an API key, so you can only obtain it from this page.
LastPass
The LastPass integration requires you to first install the LastPass CLI and add it to the PATH. This executable is not included in the normal LastPass installation, so you will have to install it manually.
Once the lpass command is set up, you will first have to log in initially when XPipe first calls the command.
Then, XPipe will be able to retrieve passwords from LastPass during the session using the case-sensitive entry name.
Enpass
The Enpass integration requires you to first install the community-made Enpass CLI and add it to the PATH. This executable is not included in the normal Enpass installation, so you will have to install it manually.
Once the enpass-cli command is set up, you will have to locate your vault.json file. You can find this file at Enpass Settings -> Advanced -> Data location.
XPipe will initially prompt for the master password when Enpass is first used during a session. Then, XPipe will be able to retrieve passwords from Enpass during the session using the entry's item name.
Windows credential manager
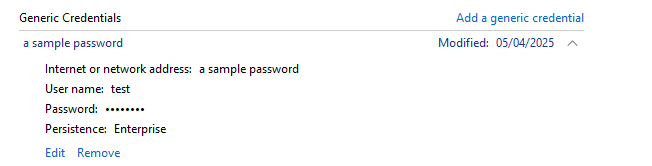
On Windows, you have access to the legacy Windows credential manager:
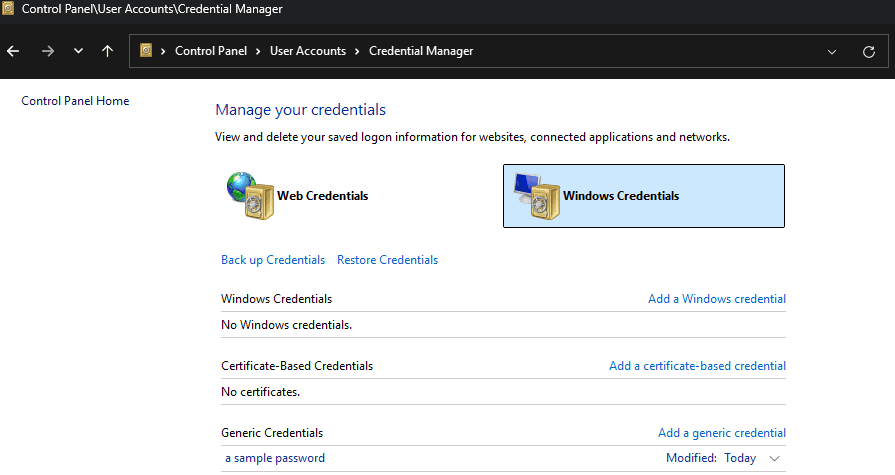
XPipe can retrieve passwords that are stored in the Generic Credentials section from it by referencing the credential title:
Custom command
If you are using a password manager solution that is not supported by a dedicated integration, there's still the option of specifying a custom command to run to retrieve passwords.
The idea is to specify a command template using the placeholder $KEY, which will be replaced by the password reference key. For example, supplying the command mypassmgr get $KEY will be replaced with mypassmgr get "sample-login" by XPipe when the command executed. Any kind of shell command syntax is supported, including features like pipes, redirects, multiline commands, and more.
An important aspect to consider when using a custom command is that XPipe can't supply any user inputs like a vault password when using it. This means that if your password manager CLI requires the user to enter some form of unlock password, it won't work. The command will not finish and that case and stays stuck. You might be able to work around this limitation by handling the password input either via some form of file or an askpass tool.
Using credentials
Secrets stored in your password manager can be used whenever credentials are required in XPipe. This can be either a username and password pair, or only a password / secret.
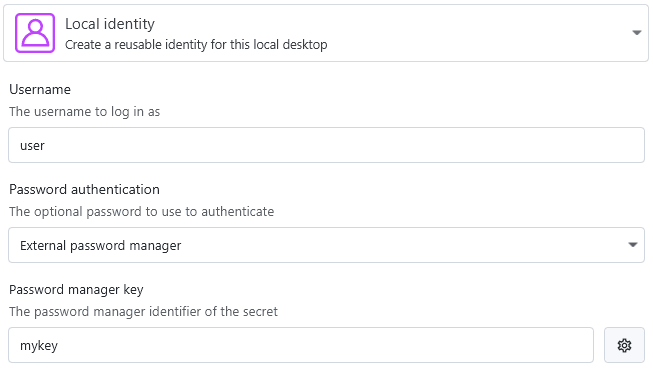
Using passwords
When creating an identity for connections, you can choose to only retrieve the password itself by choosing to use the password manager to fill the password:
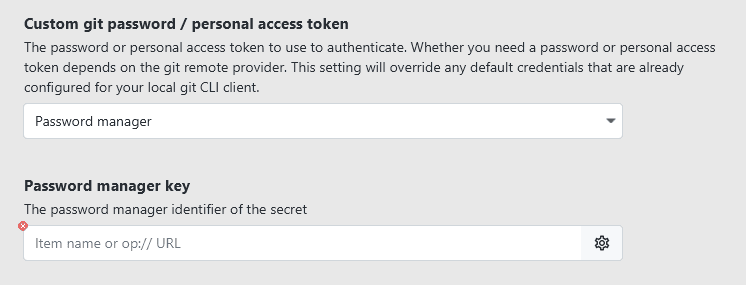
You can choose this option for any kind of secret field in XPipe, it does not have to be a password for a remote connection:
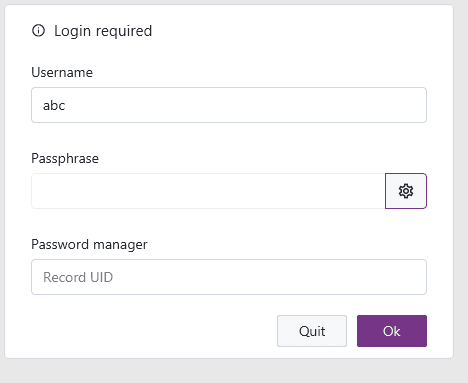
If you are making use of vault users to encrypt vault data, your password manager can also be used to supply the passphrase:
Using credentials
If your password manager entries also store usernames, you can fill in both username and password for connection identities by using password manager identities:
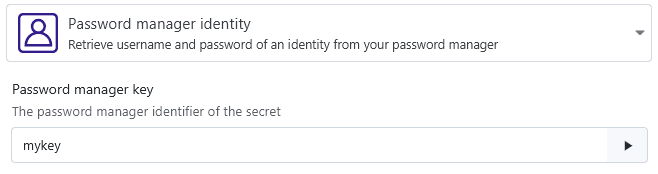
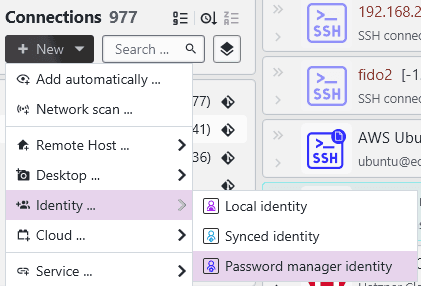
The option to create these kind of identities will show up in the creation menu once a password manager is configured:
SSH agents
Some password managers also come with functionality to supply SSH keys directly to your SSH client via their own SSH agent. For example, 1password supports this:
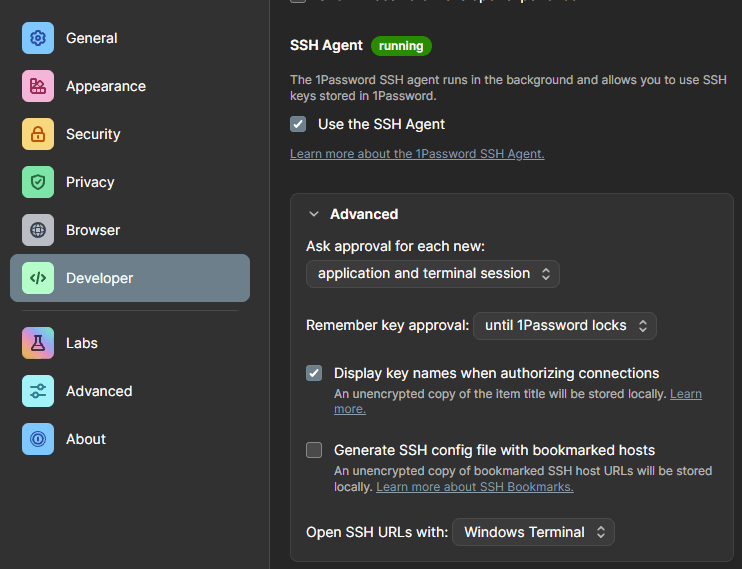
Setup
XPipe can allow you to use this agent with the right configuration. SSH connections can be configured to use this custom agent on Linux and macOS in the SSH settings:
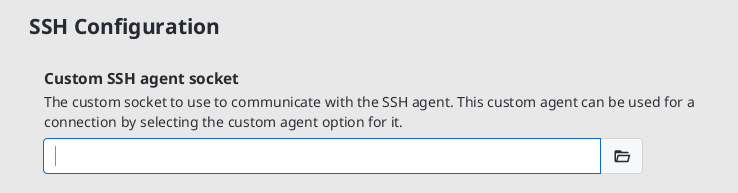
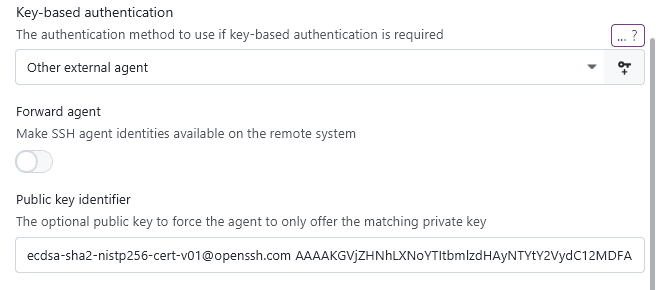
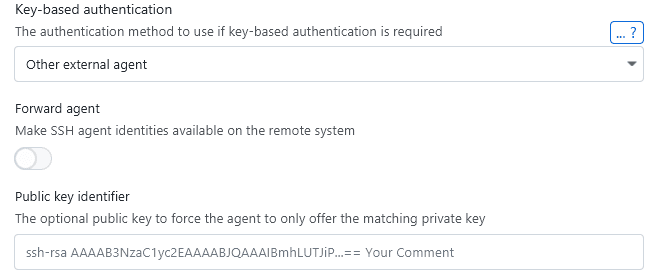
On Windows, there is no custom agent option as all agents share the same socket. To use another agent on Windows, you can use the external agent option:
Agent state
In practice, XPipe doesn't have any control over the agent. This means that you have to make sure that it is correctly configured, e.g. with environment variables, so that the agent works fine in a normal terminal session. Refer to your password manager documentation for this. XPipe can't start/stop this external agent, so you have to make sure that it is running beforehand.
If the agent is correctly configured and a connection is configured to use the password manager agent, XPipe will make sure that there aren't any conflicts with other running agents and that the agent is working. This is the best XPipe can do.
Referencing keys
One downside of agents is that by default, they will attempt to offer all available keys one-by-one until one matches. This can lead to authentication failures and exposing keys you don't want to be exposed to all remote systems.
When using the external password manager agent for authentication, you have the ability to specify the public key of the associated key pair to make the agent only use the associated private key: